Build strong
cyber culture
Engaging Cyber Security Training
Develop Competencies and Cultivate a Cyber Mindset
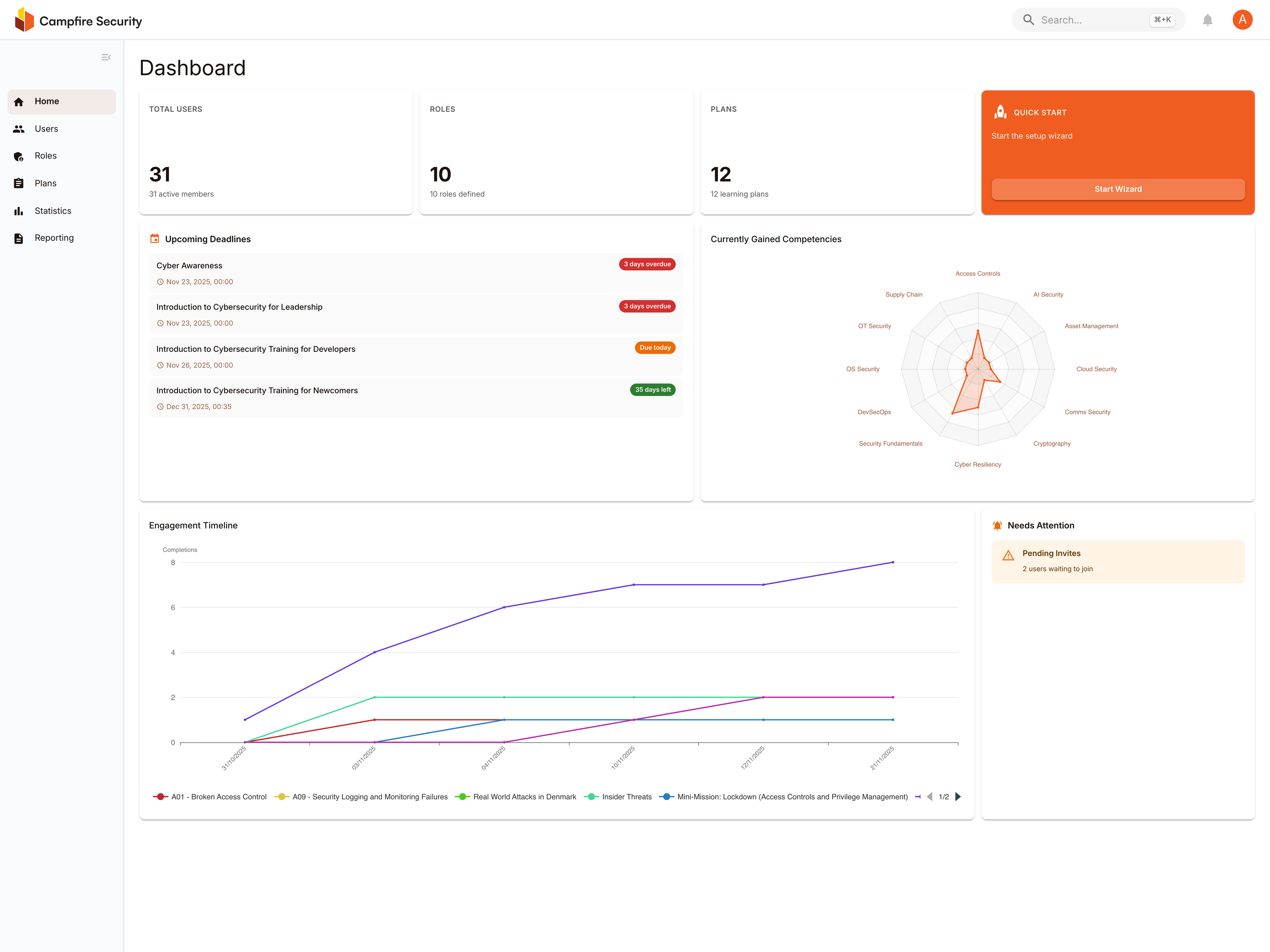


The Cyber Training Platform for Transparent Compliance
Instant Reports on Skills, Progress and Development
Build strong Cyber Culture across your organization
Want to know more?
No. 1
Danish CEOs see cyber risk as the biggest threat to their company in the coming year.
PwC CEO Survey 202569%
69% of SMEs that invest in cybersecurity experience a competitive advantage.
Industriens Fond Cyberbarometer 2024$9.5 trillion
If cybercrime were a country, its economy would be the world's third largest.
Bloomberg QuickSightTrusted by forward-thinking organizations
Because they know we care
Measure and Improve Results
Track your progress with our Cyber KPI Framework
We offer a complete system
and take care of every role in your organization

Build strong Cyber Culture through
Cyber Security competences
Simple, Intuitive, Efficient
To provide a high-level understanding of the organizational cyber security posture, strategic risks, governance, compliance, and the business impact of cyber threats.
R&D


Key Competencies
- Supply Chain Security
- DevSecOps & Software Security
IT Department


Key Competencies
- Access Controls
- Operating Systems (OS) Security
Legal Department


Key Competencies
- Cyber Security Fundamentals
- Artificial Intelligence (AI) Security
One Click
Everything You Need, in One Place
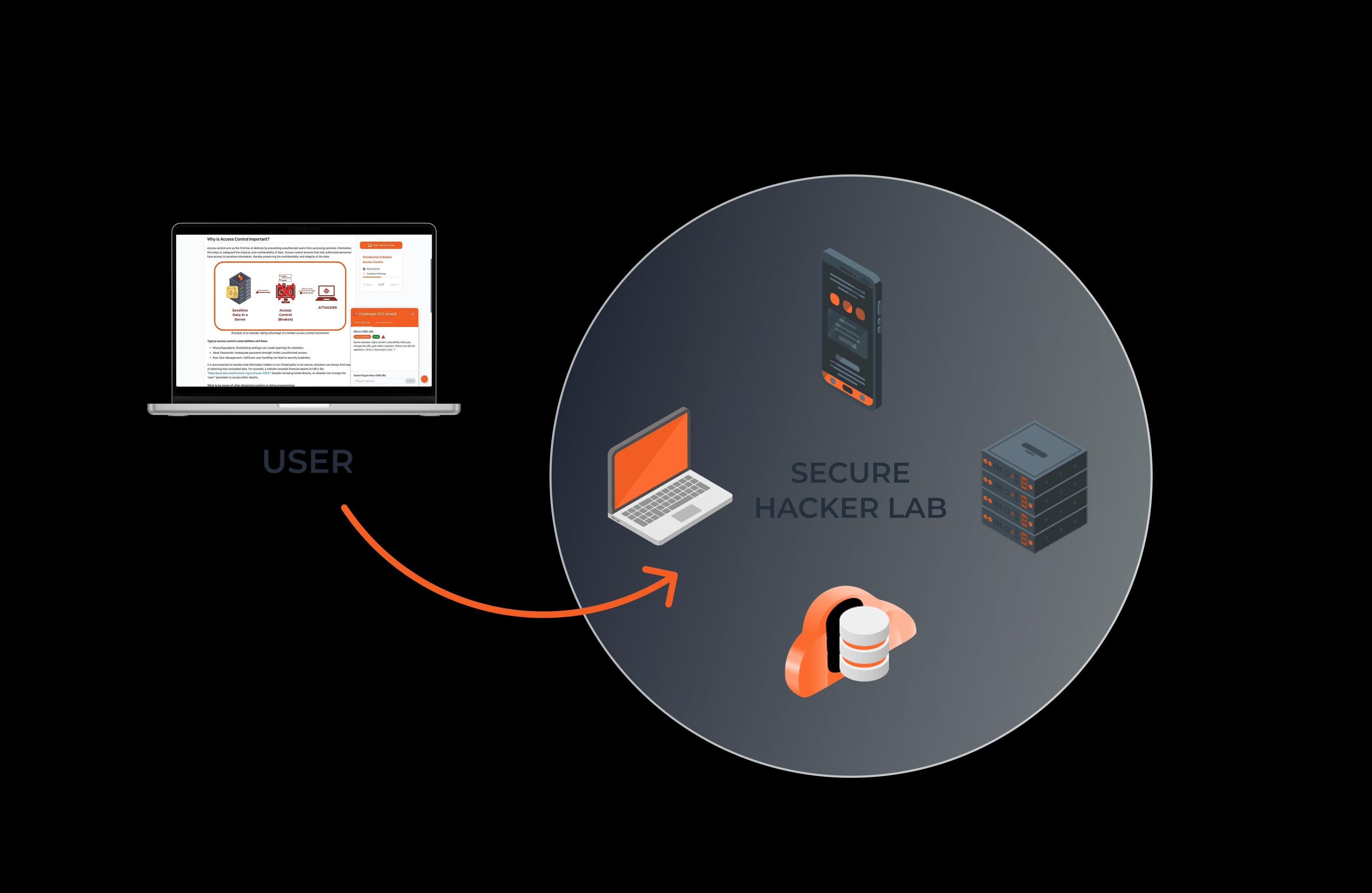
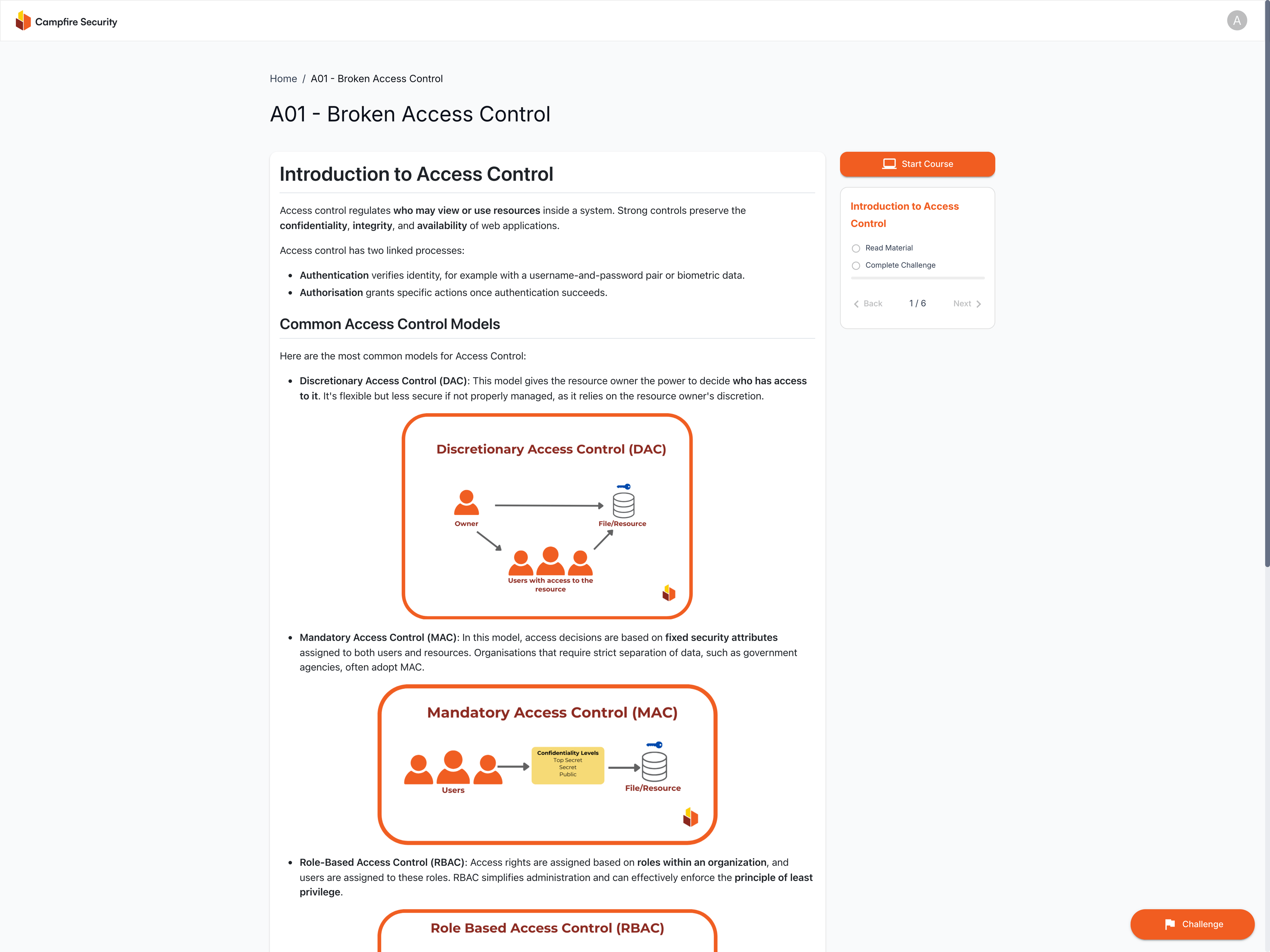
Access Hacker Labs with One Click
Dive into the Platform
Watch our video to see the platform in action.
Want to know more?
Develop skills and unlock potential
Capable employees need certifications



















































We follow a structured approach
Once enrolled everything is automated
Book
Book a short online meeting to get started
Validate
Validate the concept through a pilot setup
Implement
Implement the solution across your organization
Book
Book a short online meeting to get started
Validate
Validate the concept through a pilot setup
Implement
Implement the solution across your organization
Feel the impact
What is Cyber Culture?
People can be an organization's strongest defense – or its greatest vulnerability. Human error is the leading cause of data breaches worldwide. When employee acts with security in mind, a secure Cyber Culture is established.
Every Role Included
From CEO and Seniors Leaders, to Junior Staff and New Hires
Build Strong Cyber Culture
Cybersecurity training for professionals
Role-based learning paths assigned to the right people

Learn in a secure, supportive environment
Grounded in academia and Danish cyber community

Innovation, collaboration, and gamified design
Discover real vulnerabilities instantly through your browser

Ready to transform your security posture?
Schedule a call with our team to discuss how we can strengthen your organization's security and help you succeed with confidence.


